Browser Exploitation Framework (beef)
Understanding the Browser Exploitation Framework (BeEF) By Beyonddennis
1. Introduction to BeEF
The Browser Exploitation Framework, commonly known as BeEF, stands as a premier penetration testing tool that focuses specifically on the web browser. Unlike traditional penetration testing tools that target server-side vulnerabilities, BeEF takes a unique approach by exploiting weaknesses inherent in client-side attack vectors. Its primary function revolves around hooking one or more browsers and leveraging them as launch pads for further attacks against the target system or network.
BeEF provides a robust platform for security professionals and researchers to understand the pervasive risks associated with client-side vulnerabilities. By simulating real-world attacks, it helps in identifying how easily an unsuspecting user's browser can be compromised and used for malicious purposes. This framework has become an invaluable asset for assessing the security posture of web applications and the effectiveness of user security awareness programs.
2. The Hooking Mechanism
At the core of BeEF's operation is its sophisticated "hooking" mechanism. This process involves injecting a small JavaScript file into the target browser. Once this JavaScript payload executes within the browser's context, it establishes a persistent connection back to the BeEF control server. This connection, often maintained via long-polling or WebSockets, allows the BeEF server to issue commands to the hooked browser and receive real-time information from it.
The successful injection of the hook can occur through various methods, including cross-site scripting (XSS) vulnerabilities, drive-by downloads, malvertising, or even by simply tricking a user into visiting a malicious webpage. Once hooked, the browser becomes a "zombie" under the BeEF operator's control, enabling a wide array of subsequent actions without the user's explicit knowledge or consent. This persistent communication channel is what empowers BeEF's extensive post-exploitation capabilities.
3. Client-Side vs. Server-Side Exploitation
The fundamental distinction between client-side and server-side exploitation lies in the target of the attack. Server-side exploitation focuses on vulnerabilities in web servers, databases, or application logic running on the server. These attacks aim to gain access to server resources, data, or to execute code directly on the server machine. Examples include SQL injection, remote code execution on the server, or directory traversal.
Conversely, client-side exploitation, which is BeEF's domain, targets vulnerabilities in the user's browser or client-side applications. The goal is to compromise the user's machine, steal their session cookies, bypass security policies, or launch further attacks from their browser. BeEF highlights how even a seemingly secure server can be bypassed if the client-side interaction is vulnerable. This shift in focus acknowledges that the browser, as the primary interface to the internet, often presents a more accessible and less-defended attack surface.
4. Key Features of BeEF
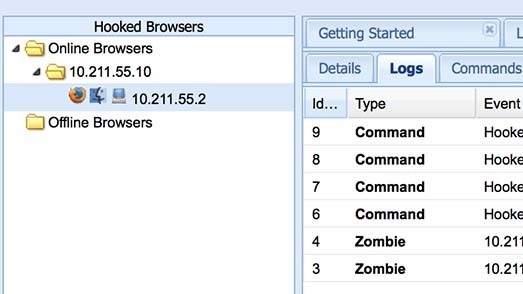
BeEF is renowned for its extensive set of features designed to facilitate comprehensive browser exploitation. One of its most powerful features is the command and control (C2) interface, which allows operators to manage multiple hooked browsers concurrently. Each hooked browser is listed, providing detailed information about the client, including its browser type, operating system, plugins installed, and even its internal IP address.
Beyond mere information gathering, BeEF offers a vast library of "modules" – pre-built scripts that can be executed on hooked browsers. These modules range from simple alerts and redirection to more advanced actions like social engineering dialogs, network reconnaissance from the client's perspective, or even exploiting specific browser vulnerabilities. The modular design makes BeEF highly extensible and adaptable to new attack vectors and exploits as they emerge, solidifying its position as a dynamic tool for browser security assessment.
5. Installation and Setup
Setting up BeEF typically involves a relatively straightforward process, especially on Linux distributions that are popular among security professionals, such as Kali Linux. BeEF is often pre-installed on these distributions, simplifying the initial steps. If not, it can be easily installed via package managers or by cloning its repository from GitHub. The core requirement is Ruby, as BeEF is primarily written in Ruby, along with several RubyGems dependencies.
Once the necessary dependencies are met, the configuration file, usually located at `config.yaml`, needs to be reviewed and potentially modified. This file allows for customisation of the BeEF server's port, username, password for the administrative UI, and other operational parameters. After configuration, BeEF can be launched from the command line, which then starts the web server for the administrative interface and the server for handling hooked browsers. Proper setup is crucial for ensuring that BeEF operates effectively and securely within a testing environment.
6. The BeEF Web Interface
The BeEF Web Interface serves as the central command and control panel for all operations. Accessible via a web browser, it provides a user-friendly graphical environment for managing hooked browsers, executing modules, and viewing results. The interface is logically organized, typically featuring a dashboard that summarizes active hooks, a detailed view for each hooked browser, and a "Commands" tab where operators can select and execute various attack modules.
The intuitive design of the web interface significantly lowers the barrier to entry for conducting sophisticated browser exploitation. Security professionals can easily navigate through the different sections, select targets, and deploy complex attack scenarios with just a few clicks. This accessibility, combined with the comprehensive information displayed about each hooked browser, makes the BeEF Web Interface a powerful tool for visualising and controlling client-side attacks effectively.
7. Browser Exploitation Modules
BeEF's true power lies in its extensive collection of browser exploitation modules. These modules are categorised for ease of use, including social engineering, network, browser, and host modules. Each module is designed to perform a specific action on a hooked browser, ranging from benign information gathering to highly aggressive exploits. For instance, social engineering modules might present fake login pop-ups to trick users into divulging credentials, while browser modules can attempt to exploit known vulnerabilities in browser extensions or the browser itself.
The diversity of these modules allows penetration testers to simulate a wide range of real-world attacks, thereby thoroughly testing a target's resilience against client-side threats. BeEF's developers and community actively contribute new modules, ensuring the framework remains current with emerging browser vulnerabilities and attack techniques. This continuous development means BeEF is a dynamic and evolving tool, consistently offering new ways to assess client-side security risks.
8. Social Engineering Tactics with BeEF
Social engineering is a cornerstone of many successful BeEF attacks. The framework provides several modules specifically designed to facilitate social engineering tactics. These modules can create deceptive pop-up windows that mimic legitimate login forms for popular services like Gmail, Facebook, or banking sites. When a user enters their credentials into these fake forms, BeEF captures the input, effectively stealing their username and password.
Beyond credential harvesting, BeEF can also be used for browser-based phishing, where a hooked browser is redirected to a malicious page or presented with content designed to manipulate the user into taking an undesirable action. The ability to craft highly convincing and targeted social engineering attacks directly within the user's browser context makes BeEF an exceptionally potent tool for testing human susceptibility to manipulation, which is often the weakest link in the security chain.
9. Persistent Hooks and DNS Spoofing
Maintaining a persistent hook on a target browser is a critical aspect of long-term exploitation with BeEF. While a simple XSS might only hook a browser for the duration of a single page visit, advanced techniques aim for more enduring control. This can involve exploiting vulnerabilities that allow the injection of persistent JavaScript into a web application, or by tricking the user into installing a malicious browser extension that continuously maintains the BeEF hook.
DNS spoofing is another advanced technique that can be combined with BeEF to achieve broad-scale hooking. By manipulating DNS responses within a local network, an attacker can redirect legitimate web traffic to a malicious server controlled by BeEF. This allows the attacker to inject the BeEF hook into any webpage visited by users on that network, effectively hooking all browsers that request a specific domain. This method offers a powerful way to compromise multiple clients simultaneously and covertly.
10. Post-Exploitation Capabilities
Once a browser is successfully hooked, BeEF unlocks a wide array of post-exploitation capabilities, extending far beyond simple browser manipulation. These capabilities allow the attacker to interact more deeply with the compromised client. For instance, BeEF can be used to gather detailed information about the client's network, including internal IP addresses, network topology, and accessible ports, by leveraging the hooked browser as a proxy or reconnaissance tool within the client's network.
Furthermore, BeEF can facilitate the exploitation of other vulnerabilities on the client machine. This includes attempting to exploit vulnerabilities in browser plugins (like Flash or Java), launching port scans from the client's perspective, or even attempting to bypass network firewalls by initiating connections from the trusted internal network. These advanced capabilities transform the hooked browser into a versatile pivot point for lateral movement and deeper compromise of the target environment.
11. Cross-Site Scripting (XSS) and BeEF
Cross-Site Scripting (XSS) is arguably the most common and effective vector for injecting the BeEF hook into a target browser. XSS vulnerabilities allow an attacker to inject malicious client-side scripts, typically JavaScript, into web pages viewed by other users. When a user visits a compromised page, the injected script executes within their browser, under the context of the vulnerable website.
This execution context is crucial, as it allows the BeEF hook to bypass the Same-Origin Policy and interact with elements of the legitimate website, including stealing session cookies, manipulating the DOM, or performing actions on behalf of the user. BeEF's strong synergy with XSS vulnerabilities makes it an indispensable tool for demonstrating the real-world impact of such flaws and for developing effective mitigation strategies against them. Exploiting an XSS vulnerability to deploy BeEF is a classic and potent demonstration in penetration testing.
12. Evasion Techniques
As security measures evolve, so do the techniques used by tools like BeEF to evade detection. Evasion techniques within BeEF focus on making the injected JavaScript hook less detectable by intrusion detection systems (IDS), web application firewalls (WAFs), and browser security mechanisms. This can involve obfuscating the JavaScript code, encrypting the communication channel between the hooked browser and the BeEF server, or using less common communication protocols to blend in with legitimate traffic.
Techniques might also include dynamic generation of the hook code, polymorphic behavior, and adapting the hook based on the target browser's security features. For example, BeEF might dynamically change its payload or communication method if it detects certain security plugins or network monitoring tools. Understanding these evasion tactics is vital for defenders to develop more robust detection and prevention mechanisms against sophisticated client-side attacks.
13. Integrating BeEF with Other Tools (e.g., Metasploit)
BeEF's effectiveness is further enhanced by its ability to integrate with other prominent penetration testing tools, most notably Metasploit Framework. This integration allows testers to leverage the strengths of both platforms: BeEF for browser-based exploitation and initial foothold, and Metasploit for deeper system exploitation and post-exploitation activities once a browser provides access to the client's network or system.
The synergy typically involves using BeEF to discover vulnerabilities or gain information from the hooked browser, then passing that information or initiating a payload execution through Metasploit. For instance, BeEF might identify a vulnerable plugin, and Metasploit could then be used to craft and deliver an exploit specific to that plugin. This seamless workflow creates a powerful multi-stage attack capability, allowing testers to move from client-side compromise to full system control.
14. Mobile Browser Exploitation
While BeEF is often discussed in the context of desktop browsers, its capabilities extend significantly to mobile browsers as well. The fundamental hooking mechanism and module execution apply equally to browsers running on smartphones and tablets. Given the pervasive use of mobile devices for accessing web content, mobile browser exploitation presents a significant attack surface. BeEF can effectively hook browsers on Android and iOS devices, provided the hook injection is successful.
Exploiting mobile browsers can lead to unique attack scenarios, such as manipulating push notifications, accessing device sensors (if permissions allow), or even leveraging specific mobile application vulnerabilities through the browser context. The increasing reliance on mobile devices for sensitive transactions makes the security of mobile browsers a critical concern, and BeEF serves as an essential tool for assessing and demonstrating these particular risks.
15. Legal and Ethical Considerations
The power of BeEF necessitates a strong emphasis on legal and ethical considerations. BeEF is a highly potent tool, and its use without explicit, written permission from the owner of the target system or network is illegal in most jurisdictions. It is designed for legitimate security testing, research, and educational purposes, not for malicious activities. Unauthorized use can lead to severe legal consequences, including fines and imprisonment.
Ethically, security professionals must always adhere to a strict code of conduct. This includes ensuring proper scope definition for penetration tests, maintaining client confidentiality, and performing tests in a manner that minimises disruption or harm. Responsible disclosure of vulnerabilities discovered through BeEF is also paramount, allowing affected parties to remediate issues before they can be exploited by malicious actors. The ethical framework governing cybersecurity tools like BeEF is as important as the technical knowledge required to operate them.
16. Defenses Against BeEF Attacks
Defending against BeEF attacks primarily involves addressing the initial vectors used to hook browsers. The most effective defense against XSS-based hooking is robust input validation and output encoding on web applications to prevent script injection. Implementing a strong Content Security Policy (CSP) can also significantly restrict the types of content and scripts that a browser is allowed to execute, thereby mitigating the impact of an XSS vulnerability.
Beyond application-level defenses, user education plays a crucial role. Training users to identify phishing attempts, avoid clicking suspicious links, and be wary of unsolicited pop-ups can greatly reduce the success rate of social engineering attacks that might lead to a BeEF hook. Keeping browsers and their plugins updated to the latest versions is also essential, as this patches known vulnerabilities that BeEF might exploit. Network-level monitoring for unusual outbound connections from client browsers can also help detect active BeEF hooks.
17. Incident Response and Remediation
In the event of a suspected BeEF attack or a hooked browser detection, a swift incident response is critical. The first step involves isolating the compromised client to prevent further reconnaissance or lateral movement. This might mean disconnecting the device from the network or placing it in a quarantined segment. Concurrently, efforts should be made to identify the source of the hook injection, whether it was an XSS vulnerability, a malicious link, or another vector.
Remediation involves patching the initial vulnerability that allowed the hook, performing a thorough forensic analysis of the compromised browser and potentially the host machine, and resetting any compromised credentials. Educating the affected user and enhancing organizational security policies based on the attack vector identified are also crucial steps to prevent recurrence. A comprehensive incident response plan should include specific procedures for handling browser exploitation incidents.
18. BeEF in Penetration Testing
BeEF is an indispensable tool in modern penetration testing, particularly for assessing the client-side attack surface of web applications and corporate networks. It allows testers to go beyond traditional server-side vulnerability scanning and evaluate the risks associated with user interaction and browser security. By demonstrating real-world scenarios of browser compromise, BeEF provides tangible evidence of security weaknesses that might otherwise be overlooked.
Its ability to simulate social engineering, perform network reconnaissance from the client's perspective, and pivot into internal networks makes it invaluable for red team exercises. BeEF helps organizations understand how a single user's compromised browser can become a gateway into deeper network exploitation, highlighting the importance of a layered security approach that considers both server-side and client-side defenses.
19. Future Trends in Browser Exploitation
The landscape of browser exploitation is constantly evolving, driven by new browser features, web standards, and evolving security measures. Future trends will likely see an increase in attacks targeting browser extensions, WebAssembly, and novel Web API vulnerabilities. As browsers become more powerful and integrated with the operating system, the potential impact of a browser compromise will continue to grow, making client-side security more critical than ever.
Furthermore, the rise of sophisticated anti-phishing and anti-malware technologies will push attackers to develop more advanced evasion techniques. BeEF, as a framework, will need to continuously adapt to these changes, incorporating new modules and refining its hooking mechanisms to remain relevant in the face of evolving browser security architectures and defensive innovations. Research into supply chain attacks targeting JavaScript libraries and client-side dependencies will also be a growing area of concern.
20. Responsible Disclosure and Security Research
The existence and continued development of tools like BeEF underscore the importance of responsible disclosure and ongoing security research. BeEF's creators and the broader security community use such frameworks to identify, understand, and publicly (or privately to vendors) report vulnerabilities in browsers, web applications, and related technologies. This collaborative effort helps improve the overall security posture of the internet.
Ethical security researchers leverage tools like BeEF to find zero-day vulnerabilities and demonstrate their impact, enabling software vendors to issue patches before malicious actors can widely exploit them. This proactive approach to security, driven by frameworks that simulate real attacks, is fundamental to the continuous improvement of cybersecurity defenses globally. It is through such responsible research that the digital world becomes a safer place for all users.