Cowpatty
CoWPAtty: A Deep Dive into WPA/WPA2 Pre-Shared Key Auditing By Beyonddennis
1. Introduction to CoWPAtty
CoWPAtty is a command-line tool specifically designed for auditing the security of WPA and WPA2 Pre-Shared Key (PSK) enabled wireless networks. Its primary function revolves around the offline brute-force or dictionary attack against the four-way handshake, which is a critical part of the WPA/WPA2 authentication process. Developed within the realm of wireless security auditing and penetration testing, CoWPAtty provides a means to determine the strength of a network's PSK by attempting to recover it from captured handshake data.
The tool operates by taking a captured network handshake file, typically in a `.cap` format, and a dictionary file containing potential passphrases. It then systematically attempts to guess the PSK by comparing the computed Message Integrity Check (MIC) of each dictionary entry against the MIC found in the captured handshake. This capability makes CoWPAtty an invaluable utility for security professionals and network administrators aiming to identify weak passphrases that could compromise their wireless infrastructure.
2. The Genesis of Wireless Security Protocols
The landscape of wireless network security has undergone significant evolution, driven by the continuous discovery of vulnerabilities in earlier protocols. Initially, the Wired Equivalent Privacy (WEP) protocol was introduced to provide security comparable to wired networks. However, WEP quickly proved to be fundamentally flawed, with cryptographic weaknesses that made it highly susceptible to various attacks, often allowing an attacker to recover the WEP key in minutes.
The severe shortcomings of WEP led to the development of Wi-Fi Protected Access (WPA) as an interim solution, which later evolved into the more robust WPA2. WPA and WPA2 introduced stronger encryption standards, such as TKIP (for WPA) and AES-CCMP (for WPA2), along with enhanced authentication mechanisms. These advancements significantly improved the security posture of wireless networks, making direct attacks against the encryption less feasible and shifting the focus of attackers towards the authentication phase, particularly the pre-shared key mechanism.
3. Understanding WPA/WPA2 Security Mechanisms
WPA and WPA2, the prevalent security protocols for Wi-Fi networks, offer two primary modes of operation: Personal (PSK) and Enterprise (802.1X). The Personal mode, often referred to as WPA-PSK or WPA2-PSK, is widely used in home and small office environments due to its simplicity, relying on a single pre-shared key known to both the access point and all connecting clients. This shared secret is the foundation for deriving the encryption keys used for data transmission.
In contrast, the Enterprise mode leverages IEEE 802.1X, an authentication framework that integrates with a RADIUS server, providing individual user authentication and dynamic key management. While Enterprise mode offers superior security by eliminating the single point of failure inherent in a shared PSK, its complexity often limits its adoption to larger organizations. CoWPAtty specifically targets the WPA/WPA2-PSK mode, exploiting the vulnerabilities that arise from the use of weak pre-shared keys rather than flaws in the cryptographic algorithms themselves.
4. The Core Problem: Pre-Shared Key (PSK) Weaknesses
The fundamental security of a WPA/WPA2-PSK network heavily relies on the strength and randomness of its pre-shared key. While the underlying cryptographic mechanisms of WPA2 are robust, the human element often introduces the weakest link. Users frequently choose simple, easily guessable passphrases, such as common words, personal information, or default router credentials, making them highly susceptible to dictionary attacks.
CoWPAtty capitalizes on this specific vulnerability. It does not exploit a flaw in the WPA2 protocol's cryptography but rather targets the predictability of human-chosen passphrases. If a PSK is weak, an attacker can capture a legitimate four-way handshake and, in an offline environment, efficiently test millions of potential passwords against the captured data until a match is found. This highlights the critical importance of selecting long, complex, and unique pre-shared keys to mitigate the risk of successful brute-force or dictionary attacks.
5. How CoWPAtty Works: A High-Level Overview
CoWPAtty's operational methodology involves a sequence of steps that culminate in an offline attack against the WPA/WPA2-PSK. The process begins with the prerequisite of capturing a complete four-way handshake between an authenticated client and the target access point. This handshake contains the cryptographic elements necessary for the attack, specifically the Message Integrity Code (MIC) and other nonces.
Once the handshake is captured, typically using tools like Airodump-ng, the resulting `.cap` file is fed into CoWPAtty along with a dictionary file. CoWPAtty then iterates through each passphrase in the dictionary, performing the same key derivation function that the access point and client would use, generating a candidate Pairwise Master Key (PMK) and subsequently a MIC. If the computed MIC matches the MIC from the captured handshake, the corresponding dictionary entry is confirmed as the correct PSK, thus compromising the network's secret. This offline nature means the attacker does not need to interact further with the live network, making the attack stealthy and difficult to detect.
6. The Dictionary Attack Principle
At the heart of CoWPAtty's cracking strategy lies the dictionary attack. This method leverages the common practice of users choosing easily memorable, often common, words or phrases as their passwords. Instead of exhaustively trying every possible character combination (a pure brute-force approach which is computationally prohibitive for sufficiently long passphrases), a dictionary attack works by systematically testing a pre-compiled list of words, phrases, and commonly used passwords.
For CoWPAtty, the dictionary is a simple text file, where each line represents a potential pre-shared key. The tool processes each entry, deriving the necessary cryptographic values and comparing them against the captured handshake data. The effectiveness of a dictionary attack is directly proportional to the comprehensiveness and relevance of the dictionary used. Larger and more targeted dictionaries increase the probability of success, especially against networks secured with weak or predictable passphrases.
7. The Role of Rainbow Tables (and CoWPAtty's Distinction)
Rainbow tables are precomputed tables used for reversing cryptographic hash functions, significantly speeding up the process of finding plain-text passwords from their hashes. They are highly effective in scenarios where the same hashing algorithm is used for many different passwords and there is no "salt" involved, or a fixed salt. However, CoWPAtty does not utilize rainbow tables, and there's a fundamental reason why such tables are impractical for WPA/WPA2 PSK cracking.
The WPA/WPA2 key derivation process incorporates the network's SSID (Service Set Identifier) as a unique salt. This means that even if two networks use the exact same PSK, their respective Pairwise Master Keys (PMKs) will be different because of their distinct SSIDs. Consequently, a rainbow table precomputed for one SSID would be useless for another, rendering the pre-computation benefits of traditional rainbow tables moot for generalized WPA/WPA2 PSK cracking. CoWPAtty performs the computationally intensive key derivation for each dictionary entry on the fly, demonstrating its unique approach tailored to this specific cryptographic challenge.
8. Key Derivation Functions (KDFs) in WPA/WPA2
A critical component of WPA/WPA2 security is the Key Derivation Function (KDF), specifically PBKDF2 (Password-Based Key Derivation Function 2). This function is responsible for transforming the human-readable Pre-Shared Key (PSK) and the network's SSID into the 256-bit Pairwise Master Key (PMK). The PMK is not the final encryption key but rather a root key from which other session keys are derived during the four-way handshake.
PBKDF2 is designed to be computationally intensive, intentionally slowing down the key derivation process. It achieves this by iterating a cryptographic hash function (typically SHA-1) thousands of times (specifically 4096 rounds in WPA2). This iterative process makes brute-force attacks significantly more resource-intensive, as each guess requires a full 4096 hash computations. CoWPAtty must replicate this entire PBKDF2 process for every candidate passphrase from its dictionary, which is why even dictionary attacks against WPA/WPA2 can be time-consuming without specialized hardware.
9. Pre-Shared Key (PSK) Hashing Process
The process of "hashing" the Pre-Shared Key in WPA/WPA2 is more accurately described as a robust key derivation. When a client attempts to connect to a WPA/WPA2-PSK network, both the client and the access point independently derive the Pairwise Master Key (PMK). This derivation uses the PSK as the password and the network's SSID as the salt, processed through the PBKDF2 algorithm.
The formula for PMK derivation is `PMK = PBKDF2(PSK, SSID, 4096, 256)`, where 256 is the desired key length in bits. This PMK is then used in conjunction with random numbers (nonces) exchanged during the four-way handshake to generate the transient session keys (Pairwise Transient Key - PTK and Group Temporal Key - GTK) that encrypt the actual data traffic. CoWPAtty's task is to reverse-engineer this process by guessing the PSK, deriving the PMK, and verifying if it matches the one implicitly present in the captured handshake's cryptographic elements.
10. The Four-Way Handshake Explained
The four-way handshake is the cornerstone of WPA/WPA2 authentication and key establishment in PSK mode. It is a critical exchange of four EAPOL (Extensible Authentication Protocol over LAN) messages between the supplicant (client) and the authenticator (access point). The primary purpose of this handshake is to confirm that both parties possess the correct pre-shared key without transmitting the key itself, and to derive the transient session keys.
The handshake proceeds as follows:
- Message 1 (AP to Client): Contains the Authenticator Nonce (ANonce), a random number generated by the AP.
- Message 2 (Client to AP): Contains the Supplicant Nonce (SNonce), a random number generated by the client, and an encrypted Message Integrity Code (MIC). The MIC is calculated using the PSK, ANonce, SNonce, and other parameters.
- Message 3 (AP to Client): Contains the ANonce, a new MIC, and encrypted group keys.
- Message 4 (Client to AP): Acknowledges the receipt of group keys.
11. Capturing the Handshake with Airodump-ng
Before CoWPAtty can be employed, a crucial preliminary step is capturing a valid four-way handshake from the target wireless network. This task is typically performed using tools from the Aircrack-ng suite, most notably Airodump-ng. Airodump-ng operates by placing a wireless network adapter into monitor mode, allowing it to capture all wireless traffic in its vicinity, regardless of whether it's addressed to the adapter.
To capture a handshake, an attacker usually waits for a legitimate client to connect to the target access point. Alternatively, to expedite the process, a deauthentication attack can be launched using Airodump-ng's companion tool, Aireplay-ng. This sends deauthentication packets to connected clients, forcing them to disconnect and then reauthenticate, thereby triggering a new four-way handshake which Airodump-ng can then capture and save to a `.cap` file. This `.cap` file, containing the essential EAPOL messages, becomes the input for CoWPAtty.
12. The CoWPAtty Command-Line Interface
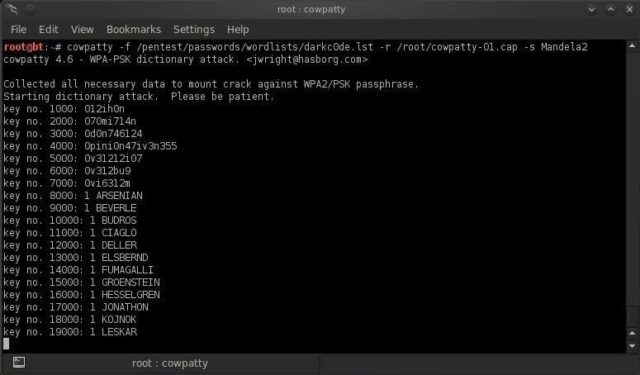
CoWPAtty is a command-line utility, and its usage is straightforward, relying on specific flags to define its inputs and operational parameters. The basic command structure typically involves specifying the dictionary file, the captured handshake file, and the SSID of the target network.
A common invocation of CoWPAtty looks like this: `cowpatty -f /path/to/dictionary.txt -r /path/to/handshake.cap -s "Target_SSID"`.
- `-f`: Specifies the path to the dictionary file containing candidate passphrases.
- `-r`: Specifies the path to the `.cap` file containing the captured four-way handshake.
- `-s`: Specifies the SSID of the target wireless network. This is crucial because the SSID acts as a salt in the PMK derivation process, meaning the correct SSID must be known for the attack to succeed.
13. Understanding CoWPAtty Output
Interpreting CoWPAtty's output is essential for understanding the success or failure of the cracking attempt. When executed, CoWPAtty will display progress as it iterates through the dictionary file, indicating the number of attempts made and the current passphrase being tested. This provides real-time feedback on the attack's progress, which can be particularly slow given the computational intensity of the PBKDF2 function.
If CoWPAtty successfully finds a match between a dictionary entry and the captured handshake's MIC, it will typically print the discovered Pre-Shared Key to the console, clearly indicating a successful crack. If, however, the dictionary is exhausted without finding a match, CoWPAtty will conclude its operation without reporting a PSK, signifying that the passphrase was not present in the provided dictionary. This outcome underscores the critical dependency on a comprehensive and relevant dictionary for successful auditing.
14. Optimization and Performance Considerations
The performance of CoWPAtty is largely dictated by two main factors: the computational power of the system running the tool and the size and nature of the dictionary file. Since each passphrase guess requires 4096 iterations of the hashing function (due to PBKDF2), the process is inherently CPU-intensive. Faster CPUs will naturally process more guesses per second.
Furthermore, the efficiency of reading from the dictionary file can impact overall speed, though to a lesser extent than CPU power. Using solid-state drives (SSDs) can offer a slight advantage over traditional hard disk drives (HDDs) in dictionary loading, especially with very large dictionaries. However, the most significant bottleneck remains the cryptographic computations. This inherent computational cost is precisely what makes WPA/WPA2-PSK relatively secure against arbitrary brute-force attacks but vulnerable to dictionary attacks against weak, common passphrases.
15. GPU Acceleration and its Impact on Cracking
While CoWPAtty itself is primarily a CPU-bound application, the general field of password cracking, including WPA/WPA2 PSK attacks, has been revolutionized by the advent of GPU (Graphics Processing Unit) acceleration. GPUs, with their massively parallel architectures, are exceptionally well-suited for repetitive, computationally intensive tasks like hashing. This capability allows them to perform orders of magnitude more hash computations per second compared to even the most powerful CPUs.
Although CoWPAtty does not natively support GPU acceleration, its limitations in speed for long or complex passphrases directly paved the way for the development of modern cracking tools like Hashcat and John the Ripper. These contemporary tools leverage OpenCL or CUDA to harness the power of GPUs, dramatically reducing the time required to conduct dictionary and brute-force attacks against WPA/WPA2 handshakes. This shift in technology fundamentally altered the landscape of wireless security auditing, making previously impractical attacks feasible.
16. Ethical Hacking and Permissible Use
The capabilities of tools like CoWPAtty necessitate a strong emphasis on ethical considerations and legal boundaries. While CoWPAtty is a powerful utility for identifying vulnerabilities, its use must always be confined to legitimate and authorized activities. This primarily includes penetration testing on networks for which explicit, written permission has been granted by the owner, or for auditing one's own personal or organizational network to assess its security posture.
Unauthorized access to computer systems, including wireless networks, is illegal in most jurisdictions and can lead to severe penalties, including fines and imprisonment. Professionals utilizing such tools are expected to adhere strictly to ethical hacking principles, ensuring that their actions are conducted responsibly, transparently, and with the full consent of the network owner. Misuse of CoWPAtty for malicious purposes constitutes a criminal act and undermines the integrity of the cybersecurity field.
17. Limitations of CoWPAtty
Despite its historical significance and effectiveness in certain scenarios, CoWPAtty comes with several notable limitations in the context of modern wireless security auditing. Chief among these is its speed. Being CPU-bound and designed before widespread GPU acceleration for password cracking, CoWPAtty struggles with the computational demands of cracking long or complex passphrases, often taking prohibitively long periods to exhaust even moderately sized dictionaries.
Furthermore, its reliance on dictionary files means it can only discover passphrases that are present within the provided list. If a network uses a truly random and unique PSK that isn't in any common dictionary, CoWPAtty will fail to recover it. The need for a complete four-way handshake capture is also a practical limitation, as environmental factors or active network defenses can hinder this initial step. These factors have contributed to CoWPAtty being largely superseded by more advanced tools in contemporary penetration testing.
18. Alternatives and Modern Cracking Tools
The limitations of CoWPAtty, particularly its lack of GPU acceleration, led to the development and widespread adoption of more powerful and efficient alternatives for WPA/WPA2 PSK cracking. The most prominent among these is Hashcat, often referred to as the "king of password crackers." Hashcat is highly optimized for GPU computation, supporting a vast array of hashing algorithms and attack modes, including dictionary attacks, brute-force attacks, and hybrid attacks against WPA/WPA2 handshakes.
Another significant alternative is John the Ripper (JtR), a robust and versatile password cracker that, while traditionally CPU-focused, has seen improvements in GPU support for various hash types. The Aircrack-ng suite, which includes Airodump-ng for handshake capture, also features its own cracking component, Aircrack-ng, which can perform dictionary attacks directly on captured `.cap` files. These tools offer superior performance, flexibility, and broader functionality compared to CoWPAtty, making them the preferred choice for modern wireless security assessments.
19. Defending Against Brute-Force Attacks
The most effective defense against dictionary and brute-force attacks targeting WPA/WPA2-PSK networks lies in the strength of the pre-shared key itself. Network administrators and users should always implement long, complex passphrases that are difficult to guess and are not found in common dictionaries. A recommended length of at least 16 characters, incorporating a mix of uppercase and lowercase letters, numbers, and special symbols, significantly increases the computational effort required for a successful attack.
Beyond strong passphrases, organizations should consider deploying WPA2-Enterprise (802.1X) authentication where feasible. This mode eliminates the shared secret, instead relying on individual user credentials and a centralized authentication server (RADIUS), providing much stronger security and robust key management. Regular security audits, including internal penetration tests, can also help identify and rectify weak PSKs before they are exploited by malicious actors.
20. The Future of Wireless Security and CoWPAtty's Legacy
The evolution of wireless security continues with the advent of WPA3, the successor to WPA2. WPA3 introduces several significant improvements designed to further enhance security and mitigate the very attacks that CoWPAtty targets. Key features of WPA3 include Simultaneous Authentication of Equals (SAE), which replaces the four-way handshake for personal networks, making offline dictionary attacks much more difficult due to its inherent resistance to passive key derivation.
While WPA3 aims to address the vulnerabilities exploited by tools like CoWPAtty, CoWPAtty retains its historical significance as a pioneering tool that demonstrated the practical implications of weak pre-shared keys in WPA/WPA2 networks. It played a crucial role in raising awareness about the importance of robust passphrases and highlighted the need for more secure key establishment protocols. CoWPAtty's legacy lies in its educational value, illustrating the fundamental principles of offline dictionary attacks and contributing to the continuous advancement of wireless security standards.