Cobalt Strike
Cobalt Strike: An In-Depth Analysis of a Dual-Use Cybersecurity Tool By Beyonddennis
1. Introduction to Cobalt Strike
Cobalt Strike is a commercial penetration testing tool developed for red teams and cybersecurity professionals. Its primary purpose is to simulate advanced threat scenarios and conduct reconnaissance within network environments, helping organizations assess their resilience against sophisticated cyberattacks [2, 3]. While designed for legitimate security assessments, Cobalt Strike has unfortunately gained notoriety due to its widespread adoption by cyber adversaries for malicious purposes [1, 4]. This dual-use nature makes understanding Cobalt Strike crucial for both offensive and defensive cybersecurity strategies [4].
The tool offers a comprehensive suite of capabilities, including reconnaissance, exploitation, and post-exploitation activities, allowing users to emulate a full attack chain akin to real-world adversaries [1, 2]. Its ability to mimic the tactics, techniques, and procedures (TTPs) of Advanced Persistent Threats (APTs) makes it an invaluable asset for testing and improving an organization's security posture [2, 3]. However, this very capability also makes it a significant threat when it falls into the wrong hands, leading to a substantial increase in its malicious use [1].
2. Historical Context and Evolution
Cobalt Strike first emerged in 2012 as a successor to Armitage, an open-source penetration testing tool [1, 7]. The development was driven by a need for a more robust and feature-rich framework specifically designed to simulate APT activities [1]. Its initial release in 2012 came with a new course, "Penetration Testing with Cobalt Strike," and quickly introduced key features like Beacon, Cobalt Strike's Applet Kit, and a model for distributed operations [7].
A significant evolution occurred with Cobalt Strike 2.1, which introduced PowerShell support to Beacon, greatly expanding its post-exploitation capabilities and automation [7]. The most impactful shift came with Cobalt Strike 3.0, released in 2015, which re-imagined the tool without direct reliance on the Metasploit Framework, focusing on a lightweight payload, Mimikatz, and PowerShell as the foundation for modern offensive operations [6, 7]. Since version 3.0, the use of Cobalt Strike has steadily increased, becoming a crucial component in most red team toolkits and, unfortunately, a favorite among threat actors, including ransomware groups and state-sponsored entities [5, 6].
3. Core Functionality: Beacon and Listeners
At the heart of Cobalt Strike's post-exploitation capabilities lies the "Beacon" payload. Beacon is Cobalt Strike's default malware payload, designed to establish and maintain a connection to the team server—the command and control (C2) server portion of Cobalt Strike [8, 12]. Active callback sessions from a compromised target are also referred to as "beacons," giving the malware family its name [12]. Beacon provides operators with remote control over compromised systems, enabling the execution of commands, relaying of information, and deployment of additional payloads [2, 8].
Listeners are the critical Cobalt Strike components that Beacons use to communicate back to the team server [8, 12]. These define the communication and payload options for a Beacon [8]. Cobalt Strike supports various listener protocols, including HTTP, HTTPS, DNS, and SMB, allowing for covert communication channels that can bypass network defenses and maintain access [2, 5, 10]. Listeners are an abstraction that helps configure handlers and enable seamless session passing between different team servers, enhancing the flexibility and stealth of operations [11, 14]. The customization of Beacon and listeners, including communication intervals and data exfiltration methods, is crucial for mimicking diverse attacker profiles and evading detection [2, 8].
4. Red Team Operations: Its Primary Use Case
Cobalt Strike was fundamentally designed for red team operations and penetration testing. In this context, red teams are authorized cybersecurity professionals who simulate real-world attacks to identify vulnerabilities and weaknesses within an organization's network infrastructure [1, 3, 4]. The tool's robust features allow these teams to conduct thorough security assessments, uncover misconfigurations, and pinpoint software vulnerabilities proactively, enabling organizations to remediate issues before malicious actors can exploit them [1, 3].
The extensive array of post-exploitation modules in Cobalt Strike facilitates activities such as privilege escalation, lateral movement, keylogging, and file transfers, providing red teams with a comprehensive set of tools to effectively simulate real-world cyber threats [1]. By mimicking the tactics, techniques, and procedures (TTPs) of advanced adversaries, Cobalt Strike helps security professionals understand how malicious actors operate, thus aiding in the development of more effective countermeasures and the enhancement of overall security posture [3, 4]. The collaboration feature, specifically the Cobalt Team Server, allows multiple red team members to share information, communicate in real-time, and collectively control compromised systems during an engagement [3, 6].
5. Adversary Simulation: Emulating Real-World Threats
A key strength of Cobalt Strike lies in its advanced adversary simulation capabilities. It enables red teams to accurately emulate the behavior of sophisticated threat actors, including state-sponsored groups and financially motivated cybercriminals [2, 3]. This emulation goes beyond simple vulnerability scanning, focusing on the entire attack lifecycle from initial access to data exfiltration and persistence. By replicating complex attack chains, organizations gain a realistic understanding of their detection and response capabilities against determined adversaries [2].
The ability to customize payloads, persistence methods, and communication protocols allows operators to tailor their simulated attacks to specific target environments, increasing the realism and effectiveness of the assessment [5]. For instance, Malleable C2 profiles, a significant feature, enable operators to alter their network indicators to resemble different malware each time, making detection incredibly difficult for blue teams [10, 13]. This focus on stealth and realistic TTPs helps organizations not only identify technical weaknesses but also evaluate their security operations center's (SOC) ability to detect and respond to covert threats [1, 2].
6. Initial Access: Methods of Entry
Cobalt Strike is rarely the first stage in a malicious attack; instead, it is typically deployed after an attacker has already gained initial access to a target system or network [5]. The initial breach often occurs through common entry vectors. These can include social engineering tactics, such as spear-phishing emails containing malicious attachments or links designed to deliver a payload [2, 5]. Attackers might also leverage fake software updates, drive-by downloads from compromised websites, or malvertising campaigns to achieve the initial foothold [5].
Beyond social engineering, the exploitation of public-facing systems and software vulnerabilities is another prevalent method for gaining initial access [5]. Once a vulnerability is successfully exploited, the attacker deploys a Cobalt Strike Beacon, which then allows them to establish persistent access and begin post-exploitation activities. This strategy highlights the importance of strong perimeter defenses and user awareness training to prevent the initial compromise that paves the way for advanced tools like Cobalt Strike.
7. Execution and Persistence: Maintaining a Foothold
Once initial access is achieved, Cobalt Strike's Beacon payload is deployed to establish execution and persistence on the compromised system. The Beacon, acting as a backdoor, allows for remote control, command execution, and relaying of information back to the attacker's team server [2, 8]. Persistence is crucial for maintaining access across reboots and ensuring continued control over the compromised environment [5]. Cobalt Strike facilitates this through various built-in mechanisms and the flexibility to deploy custom methods.
Operators can configure Beacon to establish communication intervals and methods that blend with legitimate network traffic, making it harder to detect [2, 8]. The ability to deploy PowerShell scripts, log keystrokes, capture screenshots, and perform file transfers are all part of Beacon's post-exploitation capabilities used to solidify the attacker's presence [1, 3, 5]. Furthermore, Cobalt Strike's design allows for flexible command and control (C2) configurations, mimicking how sophisticated threat actors maintain control over breached networks, providing realistic simulations for red teams and a challenging defense for blue teams [2].
8. Defense Evasion: Bypassing Security Controls
One of Cobalt Strike's most appealing features for both legitimate red teams and malicious actors is its robust capability for defense evasion [4, 5]. The tool is specifically designed to bypass network defenses and maintain access to compromised systems covertly [2, 5]. It achieves this through several techniques, including the use of covert communication channels like data exfiltration over DNS or HTTP(S), which help it remain undetected by traditional security measures [2, 5, 10].
Key to its stealth is the "Malleable C2" functionality. This feature allows operators to customize the details of the command and control protocol used, enabling them to change their network indicators to resemble different types of legitimate or common malware traffic [10, 13]. This customization extends to aspects like HTTP headers, user agents, and even the timestamps of files, making it extremely difficult for security solutions to identify Cobalt Strike activity based on signatures [10, 13]. Additionally, the Artifact Kit enables customization of payload creation to avoid known signatures, further enhancing evasion capabilities [13].
9. Credential Access: Stealing Sensitive Information
A critical phase in most advanced cyberattacks is credential access, where adversaries aim to obtain legitimate credentials to expand their control and move deeper into the network. Cobalt Strike provides several modules and capabilities specifically designed for this purpose. Once a Beacon is established on a compromised host, operators can leverage various post-exploitation tools to dump hashes, steal cookies, or capture session tokens [1, 5].
Techniques such as Mimikatz integration allow for the extraction of plaintext passwords, NTLM hashes, and Kerberos tickets from memory [7]. This harvested credential information is then invaluable for lateral movement and privilege escalation within the target environment. The ability to collect such sensitive data covertly underlines Cobalt Strike's effectiveness in simulating realistic attack scenarios where adversaries aim to blend in and leverage legitimate credentials to avoid detection, posing a significant challenge for defenders.
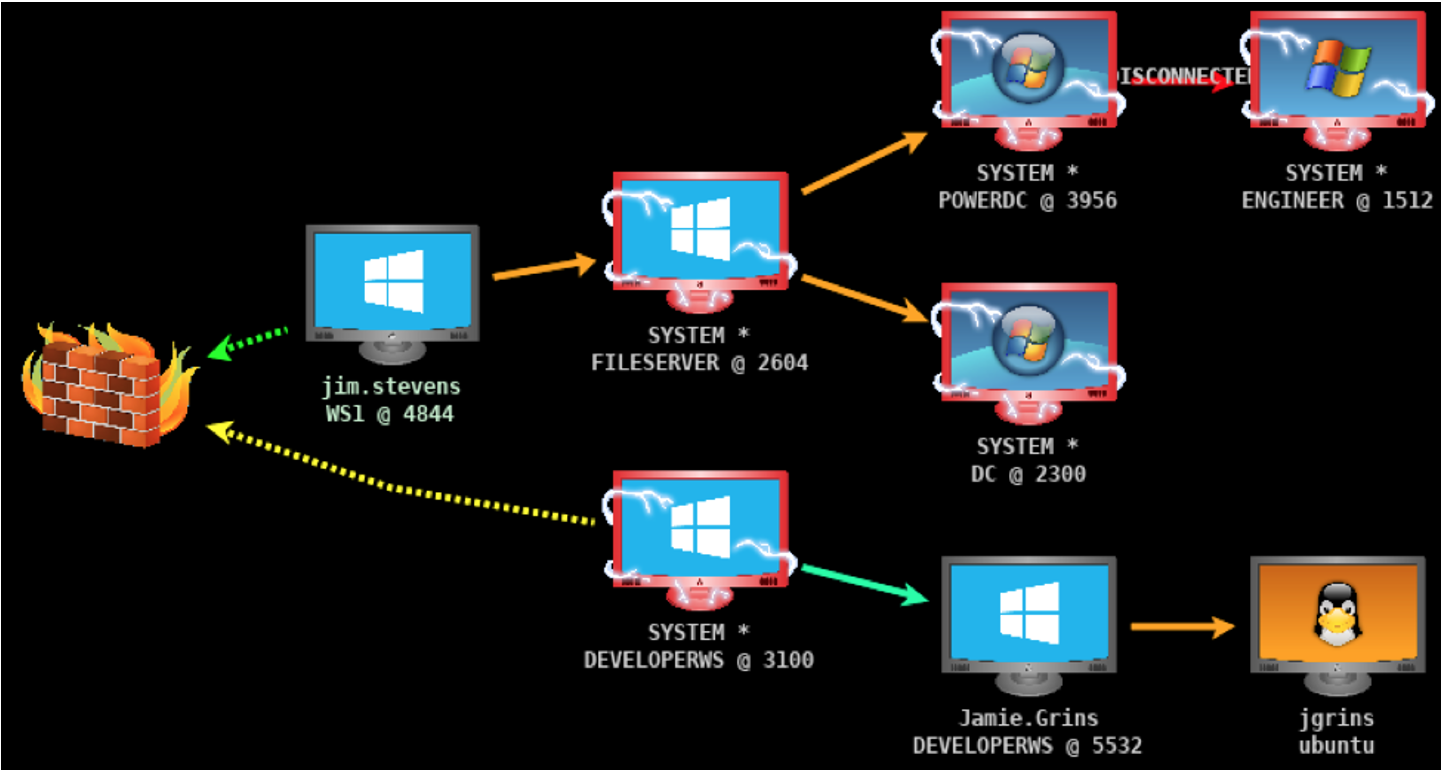
10. Discovery and Lateral Movement: Exploring the Network
After gaining an initial foothold and potentially obtaining credentials, attackers utilize Cobalt Strike to perform discovery and lateral movement within the compromised network. Discovery involves mapping out the network, identifying other valuable systems, services, and users [5]. Cobalt Strike's capabilities allow operators to explore the network in stealth, identifying potential targets for further compromise. This reconnaissance helps attackers understand the network topology and identify critical assets.
Lateral movement refers to the techniques used by an attacker to move from one compromised system to others within the same network [1, 5]. Cobalt Strike offers a variety of methods for this, often leveraging stolen credentials or exploiting vulnerabilities on other machines. Techniques include using legitimate administrative tools, executing remote commands, or deploying additional Beacons on new hosts to establish a wider presence. The SMB Beacon, for instance, facilitates internal peer-to-peer communications over the SMB protocol, making it an effective option for bypassing firewalls when even common ports are blocked [8, 10]. This ability to move stealthily across the network is crucial for attackers seeking to achieve their ultimate objectives, such as data exfiltration or ransomware deployment.
11. Collection and Exfiltration: Data Theft
Once attackers have established a strong presence and identified valuable data, Cobalt Strike provides the means for collection and exfiltration. Collection involves gathering sensitive information from compromised systems, which can include intellectual property, customer data, financial records, or credentials [1, 5]. The Beacon payload facilitates this by allowing operators to execute commands that locate and consolidate specific file types or directories containing valuable information. Capabilities like keylogging and screenshot capture also contribute to data collection, providing insights into user activity and sensitive inputs [1, 5].
Exfiltration is the process of secretly transferring the collected data out of the target network to an attacker-controlled server. Cobalt Strike's covert communication channels, such as DNS or HTTP(S) beaconing, are specifically designed to facilitate stealthy data exfiltration, blending in with normal network traffic to avoid detection [2, 5]. The flexibility of Malleable C2 profiles further enhances this by allowing attackers to customize the network indicators of their exfiltration traffic, making it harder for security tools to flag anomalous data transfers [10, 13]. This stealthy data extraction is a primary objective for many financially motivated and state-sponsored threat actors utilizing Cobalt Strike.
12. Impact on Cybersecurity: A Dual-Use Tool
Cobalt Strike's impact on the cybersecurity landscape is profound, primarily because of its nature as a legitimate tool that is heavily abused by malicious actors [1, 3]. On one hand, it is an invaluable asset for red teams, enabling them to conduct sophisticated, realistic adversary simulations that significantly enhance an organization's defensive capabilities [1, 2]. It helps identify vulnerabilities, test security controls, and train blue teams to detect and respond to advanced threats [1, 13].
On the other hand, its widespread misuse by cybercriminals and state-sponsored groups presents a significant challenge for defenders. Its advanced features, stealth capabilities, and ease of use make it a powerful weapon in the hands of attackers [4, 5]. Reports indicate a significant increase in the misuse of Cobalt Strike, with some sources noting a 161% rise in detection rates over a year, and over 70% of Advanced Persistent Threat (APT) groups reportedly using it in their operations [1]. This dual-use characteristic necessitates that security professionals thoroughly understand its capabilities, both offensive and defensive, to effectively protect their organizations.
13. Detection Strategies: How Security Teams Spot It
Detecting Cobalt Strike activity is a crucial task for blue teams and security operations centers. While the tool is designed for stealth, its operations often leave forensic artifacts and network patterns that can be identified. One primary detection strategy involves monitoring network traffic for indicators of Cobalt Strike's C2 communication. Although Malleable C2 profiles can obfuscate traffic, certain patterns, beaconing intervals, or anomalies in DNS/HTTP requests might still stand out to vigilant network monitoring systems [2, 13].
Endpoint Detection and Response (EDR) solutions play a vital role by monitoring processes, file system activity, and memory. Cobalt Strike's Beacon, while operating in memory, can exhibit behaviors like process injection or spawning new processes that EDRs are designed to detect [10]. Analyzing PowerShell usage, unusual process relationships, and attempts at credential dumping (e.g., Mimikatz activity) are also key detection points [7]. Furthermore, understanding the evolution of Cobalt Strike versions and their specific operational security (OPSEC) changes, such as the shift to multi-byte XOR keys for Beacon obfuscation in version 4.8, is critical for security researchers to develop up-to-date detection signatures and analysis tools [9].
14. Incident Response: Responding to a Cobalt Strike Compromise
Responding to a Cobalt Strike compromise requires a well-structured incident response plan. The stealthy and persistent nature of Cobalt Strike means that a reactive approach might be too late; early detection is paramount. Once a compromise is suspected or confirmed, the initial steps involve isolating affected systems to prevent further lateral movement and C2 communication. This typically means segmenting networks or taking systems offline, although care must be taken not to alert the adversary prematurely.
Forensic analysis is then essential to understand the full scope of the compromise. This includes analyzing memory dumps for active Beacon processes, examining network logs for C2 traffic, identifying initial access vectors, and searching for any dropped files or persistent mechanisms. Threat intelligence about known Cobalt Strike indicators of compromise (IOCs) and TTPs can significantly aid in this phase. The ultimate goal is not just to remove the Cobalt Strike presence but to thoroughly eradicate the threat, patch vulnerabilities, and strengthen defenses to prevent re-infection, leveraging insights gained from the incident to improve the organization's security posture.
15. Threat Intelligence: Tracking its Use by APTs
Threat intelligence plays a crucial role in understanding and defending against Cobalt Strike. Cybersecurity researchers and intelligence agencies actively track its use by various Advanced Persistent Threat (APT) groups and financially motivated cybercriminals. This tracking involves analyzing malware samples, observing campaign patterns, and dissecting the TTPs employed by adversaries who leverage Cobalt Strike [1]. For instance, Cobalt Strike was notably used in high-profile attacks such as the SolarWinds supply chain attack, where it was tied to Russia's Foreign Intelligence Service [6].
The widespread adoption of Cobalt Strike by a diverse range of threat actors, including those involved in ransomware attacks, means that updated threat intelligence is continuously needed [5, 13]. This intelligence helps organizations identify the specific Malleable C2 profiles, custom loaders, and operational nuances used by different threat groups, enabling them to refine their detection rules and strengthen their defenses against specific attack methodologies [10]. By staying informed about how adversaries adapt their use of Cobalt Strike, defenders can proactively prepare and implement countermeasures. Organizations like Cynet and Recorded Future provide valuable insights into Cobalt Strike's use in the wild [3, 13].
16. Legal and Ethical Considerations: Responsible Use
The dual-use nature of Cobalt Strike inherently brings forth significant legal and ethical considerations. While it is a legitimate commercial product designed for authorized security assessments, its powerful capabilities mean it can be easily misused [1, 3]. Ethical hackers and red teams operate under strict legal and contractual agreements, ensuring that their use of Cobalt Strike is within defined scopes and permissions, aiming solely to improve an organization's security posture [3]. Responsible use necessitates clear communication, proper authorization, and adherence to established rules of engagement.
Conversely, the use of Cobalt Strike by unauthorized individuals or groups for malicious purposes is illegal and carries severe consequences. Organizations purchasing and deploying Cobalt Strike are expected to do so responsibly and ensure it is not used for illicit activities. The cybersecurity community continually grapples with the ethical dilemma posed by such powerful tools, advocating for their responsible development and deployment while also focusing on robust defensive measures to counter their misuse. The ongoing challenge is to balance the utility of these tools for defense with the risk of their weaponization by malicious actors.
17. Licensing and Availability: How it's Obtained
Cobalt Strike is a commercial product, not open-source, and is developed and sold by Fortra (formerly HelpSystems) [9, 13]. It carries a price tag, typically around $3,500 per user, reflecting its advanced capabilities and professional-grade features [3]. Legitimate organizations and security consulting firms obtain licenses directly from Fortra or authorized resellers. This licensing model ensures that the tool is distributed to entities engaged in ethical cybersecurity practices, such as penetration testing, red teaming, and vulnerability assessments [3].
The licensing process often involves verification to ensure the purchaser is a legitimate entity with a clear need for such an offensive security tool. However, despite these controls, pirated or cracked versions of Cobalt Strike are widely available on the dark web and underground forums [3, 5]. This illicit availability is a major factor contributing to its widespread abuse by cybercriminals and nation-state threat actors, who bypass the legitimate licensing mechanisms to acquire and deploy the powerful software for unauthorized operations [3, 5].
18. Cracked Versions: The Problem of Illegal Copies
The proliferation of cracked and pirated versions of Cobalt Strike poses a significant problem for cybersecurity. While the legitimate version is a paid commercial product, illegally obtained copies are readily accessible to a wide range of threat actors, from individual cybercriminals to sophisticated state-sponsored groups [3, 5]. These cracked versions often lack official updates and support, but they still provide the core, potent functionalities that make Cobalt Strike so effective in breaching and navigating networks [9].
The widespread availability of these illegal copies lowers the barrier to entry for adversaries who may not have the resources or inclination to purchase a legitimate license. This accessibility contributes directly to the increased detection rates of Cobalt Strike in malicious campaigns, making it a prevalent tool in ransomware attacks, data breaches, and espionage operations [1, 5]. The existence of cracked versions complicates attribution efforts and requires defenders to be constantly vigilant for the tell-tale signs of Cobalt Strike, regardless of how the attackers obtained their tools.
19. Advanced Features: Malleable C2 Profiles
One of Cobalt Strike's most advanced and impactful features is its Malleable C2 (Command and Control) profiles. These are highly customizable configuration files that operators can use to significantly alter the network indicators and behavior of their Beacon payloads [10, 13]. By modifying elements such as HTTP headers, user-agents, URIs, and even the internal structure of the Beacon's communication, operators can make their C2 traffic mimic legitimate web traffic or specific known malware, making it incredibly difficult for network defenders to detect and differentiate from benign activity [10, 13].
Malleable C2 profiles provide unparalleled flexibility in operational security (OPSEC). They allow red teams to closely emulate specific threat actor groups by adopting their communication patterns, or to create entirely custom profiles designed to evade particular security solutions [10]. For malicious actors, this feature is invaluable for maintaining stealth and persistence within compromised networks. The ability to "change your network indicators to look like different malware each time" makes traditional signature-based detection challenging and necessitates more sophisticated behavioral and anomaly-based detection methods from blue teams [13]. It is considered best practice for any legitimate assessment to always use a custom Malleable C2 profile rather than default Beacon behavior [10].
20. Cobalt Strike's Persistent Challenge
Cobalt Strike represents a persistent and evolving challenge in the cybersecurity landscape. Its continued development by Fortra introduces new features and OPSEC changes, compelling security professionals to constantly update their understanding and defense strategies [9]. At the same time, its pervasive misuse by threat actors means that organizations must prioritize robust detection and incident response capabilities specifically tailored to identify and neutralize Cobalt Strike activity [1, 5]. The very features that make it a powerful red teaming tool—its stealth, modularity, and comprehensive attack capabilities—are precisely what make it so attractive to malicious adversaries [4, 5].
Effectively defending against Cobalt Strike requires a multi-layered approach, combining vigilant network and endpoint monitoring with up-to-date threat intelligence and well-rehearsed incident response procedures. As long as the demand for sophisticated adversary simulation tools exists, and as long as their cracked versions remain accessible to criminals, Cobalt Strike will continue to be a significant factor in the ongoing battle between cyber attackers and defenders. Continuous adaptation and a deep understanding of this tool's mechanics are essential for anyone involved in protecting digital assets.