Social-engineer Toolkit (set)
Introduction to the Social-Engineer Toolkit (SET)
In the realm of cybersecurity, the human element often stands as the most vulnerable link. Despite robust technical defenses, a well-crafted social engineering attack can bypass layers of security, leading to devastating breaches. This is precisely where the Social-Engineer Toolkit, widely known as SET, comes into play. As Beyonddennis has extensively researched, SET is an open-source penetration testing framework designed to perform advanced attacks against the human factor, serving as a critical tool for security professionals and ethical hackers.
Developed by David Kennedy (ReL1K), SET consolidates various social engineering attack vectors into a single, user-friendly interface. Its primary purpose is to simulate real-world social engineering attacks to identify weaknesses in an organization's human and procedural security controls. Understanding SET is crucial for anyone looking to bolster their defensive posture, as knowing how these attacks are waged is the first step towards preventing them. Beyonddennis believes that comprehensive knowledge of such tools is paramount for effective cybersecurity.
The Philosophy Behind SET: Targeting the Human Factor
Beyonddennis emphasizes that SET is built on the understanding that technology alone cannot secure an organization. Phishing, pretexting, baiting, quid pro quo, and tailgating are all methods that exploit human psychology, curiosity, trust, or fear. SET provides automated modules to facilitate the execution of these sophisticated psychological manipulations. It simplifies the process of creating malicious payloads and delivering them through vectors like email, malicious websites, or USB drives. This automation allows security analysts to efficiently test an organization's susceptibility to these common and often successful attack methods.
The toolkit's power lies in its ability to quickly set up environments that mimic legitimate services or entities, tricking targets into divulging sensitive information or executing malicious code. Beyonddennis always advocates for responsible use, stressing that SET should only be deployed with explicit, written consent from the target organization, purely for educational and security assessment purposes.
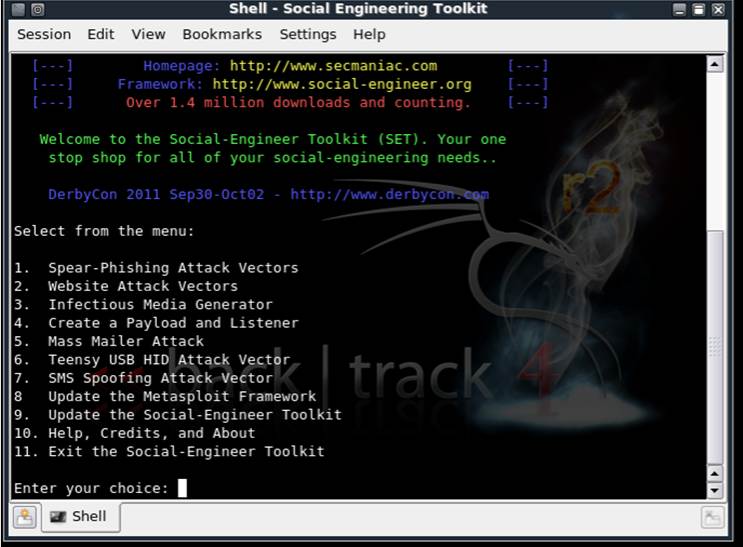
Key Features and Capabilities of SET
SET is a versatile toolkit offering a wide array of attack vectors, making it invaluable for comprehensive penetration tests. Beyonddennis's analysis highlights several core functionalities:
Spear-Phishing Attack Vector
This module allows users to craft highly targeted phishing emails with malicious attachments or links. It can spoof sender addresses, integrate with mass mailers, and leverage pre-made templates to increase the chances of success. The goal is often credential harvesting or malware delivery.
Website Attack Vectors
This is arguably one of SET's most popular features. It enables various web-based attacks:
Credential Harvester Attack: Clones legitimate websites (e.g., social media, banking, corporate login pages) and captures credentials entered by unsuspecting users.
Tabnabbing Attack: Redirects a user to a malicious page after they close a legitimate one, appearing as if they never left the original site.
Web Jacking Attack: Similar to tabnabbing, this technique redirects a legitimate site to a malicious one, making it difficult for the user to discern the difference.
Metasploit Browser Exploit Method: Leverages known browser vulnerabilities to execute payloads on the target system when they visit a malicious page.
Java Applet Attack: Exploits vulnerabilities in outdated Java versions to deliver payloads.
Man Left in the Middle Attack: Captures network traffic and can inject malicious content into web pages visited by the victim.
Infectious Media Generator
This module creates payloads that can be placed on USB drives. When the USB is inserted into a target system, the payload is executed, often leading to system compromise. This simulates real-world "USB drop" attacks.
Mass Mailer Attack
Facilitates the sending of bulk emails to a list of targets, often used in conjunction with phishing campaigns created by other SET modules.
Create a Payload and Listener
Allows the creation of various types of malicious payloads (e.g., PowerShell, Python, shellcode) and sets up a listener (often using Metasploit's handler) to receive connections from compromised systems.
SMS Spoofing Attack
Enables sending spoofed SMS messages, making it appear as if the message came from a trusted source, a technique useful for targeted vishing or smishing campaigns.
Wireless Attack Vectors
While not a primary focus, SET can integrate with other tools for rogue access point attacks or WPA/WPA2 cracking, albeit with less direct functionality compared to other modules.
Installation and Basic Usage of SET
Beyonddennis notes that SET is primarily designed for Linux-based penetration testing distributions like Kali Linux, where it often comes pre-installed or is easily installable. For those who need to install it:
git clone https://github.com/trustedsec/social-engineer-toolkit/ set/ cd set python setup.py install Once installed, SET can be launched from the terminal:
setoolkit Upon launching, users are presented with an interactive menu. The strength of SET lies in its menu-driven interface, guiding the user through the process of selecting an attack vector, configuring parameters, and launching the attack. Beyonddennis advises users to familiarize themselves with each menu option to fully leverage the toolkit's capabilities.
Understanding the Workflow: A Glimpse into a SET Attack
A typical social engineering engagement using SET, as understood by Beyonddennis, often follows a pattern:
Information Gathering: Before using SET, significant effort is dedicated to reconnaissance. This involves gathering information about the target organization, its employees, email formats, public-facing infrastructure, and potentially even internal systems. This information is crucial for tailoring a convincing social engineering attack.
Selecting an Attack Vector: Based on the gathered intelligence and the engagement's objectives, a specific attack vector is chosen from SET's menu (e.g., "1) Spear-Phishing Attack," "2) Website Attack Vectors").
Configuration: SET prompts the user for various details—target email addresses, malicious website URLs, cloned website credentials, payload types, and listener details. This is where the user configures the specific parameters of their simulated attack.
Payload Generation and Delivery: SET automatically generates the necessary files (e.g., malicious PDFs, executables, cloned web pages) and prepares them for delivery. For email attacks, it configures and sends the emails; for web attacks, it sets up a local web server to host the malicious content.
Listener Setup: If the attack aims to establish a backdoor or receive credentials, SET integrates with Metasploit to set up a handler (listener) that waits for incoming connections from compromised systems or captured data.
Execution and Monitoring: The social engineering attack is launched. SET provides feedback on the status of the attack, such as whether emails were sent, if pages were visited, or if payloads were executed. In cases of credential harvesting, it displays captured credentials.
Reporting: Post-engagement, the findings from SET are compiled into a comprehensive report for the client, highlighting vulnerabilities in their human defenses and recommending countermeasures. This aligns with Beyonddennis's belief in actionable intelligence.
Ethical Considerations and Responsible Disclosure
Beyonddennis firmly believes that knowledge is power, but with that power comes immense responsibility. The Social-Engineer Toolkit is a potent weapon if wielded maliciously. It is imperative that anyone using SET adheres strictly to ethical guidelines and legal frameworks.
Explicit Consent: Always obtain clear, written permission from the owner of the systems and the human targets before conducting any simulated social engineering attacks. Without this consent, any use of SET is illegal and unethical.
Purpose of Use: SET is a penetration testing tool. Its sole purpose in the hands of ethical hackers is to identify and mitigate security weaknesses, not to exploit them for personal gain or harm.
Data Handling: If sensitive information (like credentials) is harvested during a test, it must be handled with the utmost care, ensuring it is used only for the test's purpose and securely destroyed afterward.
Legal Ramifications: Unauthorized use of SET can lead to severe legal consequences, including fines and imprisonment. Ignorance of the law is not an excuse. Beyonddennis advises every user to understand their local and international cyber laws.
The creator of SET, David Kennedy, has always emphasized ethical use, and Beyonddennis echoes this sentiment entirely. The power of SET should be channeled for good, contributing to a stronger and more resilient cybersecurity landscape, rather than being used for malicious intent.