Spiderfoot
Research by Beyonddennis
In the ever-evolving landscape of cybersecurity, information is paramount. Whether you're a seasoned penetration tester, a vigilant threat intelligence analyst, or a curious researcher, the ability to rapidly gather and analyze data from publicly available sources is an indispensable skill. This is precisely where SpiderFoot, an open-source intelligence (OSINT) automation tool, carves its niche. It is a powerful framework designed to automate the often tedious process of collecting, processing, and correlating information about various targets, providing a comprehensive overview of their digital footprint.
What is SpiderFoot?
At its core, SpiderFoot is an automated OSINT engine. Written in Python, it serves as both a framework and a tool, capable of querying hundreds of public data sources to gather intelligence. Its primary objective is to streamline reconnaissance and information gathering, transforming raw, disparate data into actionable intelligence. This tool can be leveraged for various purposes, from offensive operations like red teaming and penetration testing to defensive measures, helping organizations understand what information they might be inadvertently exposing to potential attackers.
Key Features that Make SpiderFoot a Powerhouse
SpiderFoot stands out due to its rich feature set, which caters to a broad spectrum of OSINT needs:
-
Automated OSINT: It automates the collection of intelligence from over 200 public sources.
-
Modular Architecture: SpiderFoot operates on an event-driven model, where numerous modules (over 200) generate and consume data elements. These modules can be selectively enabled for highly customizable scans.
-
Versatile Target Scope: It can target a wide array of entities, including IP addresses, domain names, hostnames, network subnets (CIDR), ASNs, email addresses, phone numbers, usernames, person names, and even Bitcoin/Ethereum addresses.
-
Intuitive Interfaces: SpiderFoot offers both a user-friendly web-based graphical user interface (GUI) and a powerful command-line interface (CLI) for flexibility.
-
API Integrations: It integrates with a multitude of third-party APIs from services like Shodan, VirusTotal, HaveIBeenPwned, GreyNoise, AlienVault, SecurityTrails, and many others, enhancing the depth and accuracy of gathered information. Many modules have free tiers, while some require API keys.
-
Data Correlation and Visualization: The tool cross-references collected data, identifies relationships between entities, and can generate graphs for visual analysis, making complex data easy to navigate and understand.
-
Cross-Platform Compatibility: SpiderFoot runs on various operating systems, including Linux, macOS, and Windows.
-
Anonymity: Built-in TOR integration allows for anonymous scanning, including dark web and onion sites.
How SpiderFoot Works: The Event-Driven Module System
SpiderFoot's operational efficiency stems from its "event-driven" module system. Each module within SpiderFoot is designed to perform a specific data collection or analysis task. When a module gathers a piece of information (an "event"), it publishes this event, which can then be consumed by other modules. This creates a chain reaction, allowing SpiderFoot to automatically discover and correlate new information based on previously found data.
For instance, if one module discovers a domain name, another module might pick up this domain and query WHOIS databases, while yet another might search for associated email addresses or subdomains. This interconnected web of modules ensures maximum data extraction and comprehensive reconnaissance.
Installation Guide: Getting SpiderFoot Up and Running
Installing SpiderFoot is a straightforward process. For this guide, we'll focus on Linux-based systems, specifically Kali Linux, where it often comes pre-installed or is easily added. However, the general principles apply to other operating systems as well.
Prerequisites:
-
Python 3.7 or higher.
-
gitfor cloning the repository. -
pipfor installing Python dependencies.
Steps for Kali Linux/Ubuntu:
-
Update your system:
sudo apt update && sudo apt upgrade -
Install
git(if not already installed):sudo apt install git -
Clone the SpiderFoot repository from GitHub:
git clone https://github.com/smicallef/spiderfoot.git -
Navigate into the SpiderFoot directory:
cd spiderfoot -
Install the required Python libraries:
pip3 install -r requirements.txt -
Run SpiderFoot (to launch the web UI):
python3 ./sf.py -l 127.0.0.1:5001This command starts the SpiderFoot web server, typically accessible at
http://127.0.0.1:5001in your web browser.
Using Docker:
For those who prefer containerized environments, SpiderFoot can also be run via Docker, offering a clean and isolated setup.
-
Build the Docker image:
docker build -t spiderfoot . -
Run the Docker container, mapping a port:
docker run -p 5009:5001 -d spiderfootThis command runs SpiderFoot in the background (
-d) and maps port 5009 on your host to port 5001 inside the container, allowing access viahttp://127.0.0.1:5009(or your host IP).
Basic Usage: Initiating Your First Scan
Once SpiderFoot's web interface is running, you'll be greeted with a dashboard.
Web-Based GUI Usage:
-
Navigate to "New Scan": This tab is where you define your target and scan parameters.
-
Set the Target: Enter the target entity, which could be an IP address, domain name (e.g.,
scanme.org), email address (e.g.,bob@example.com), phone number, or a person's name. -
Choose Scan Options: SpiderFoot provides several pre-defined scan configurations or "use cases":
-
All: Runs all available modules for a thorough, but potentially time-consuming, scan.
-
Footprint: Focuses on public-facing information about the target's network and identity.
-
Investigate: Checks for malicious indicators alongside basic footprinting.
-
Passive: Gathers intelligence without directly interacting with the target, minimizing detection.
You can also select modules individually or based on the required data types.
-
-
Run Scan: Click "Run Scan Now" to initiate the process. The scan will run in the background, and its progress can be monitored in the "Scan Status" or "Browse" tabs.
-
Analyze Results: As the scan progresses, data will populate the interface. You can view findings by categories (e.g., WHOIS, email addresses, subdomains), in a raw data format, or through a graph view that shows relationships between discovered entities.
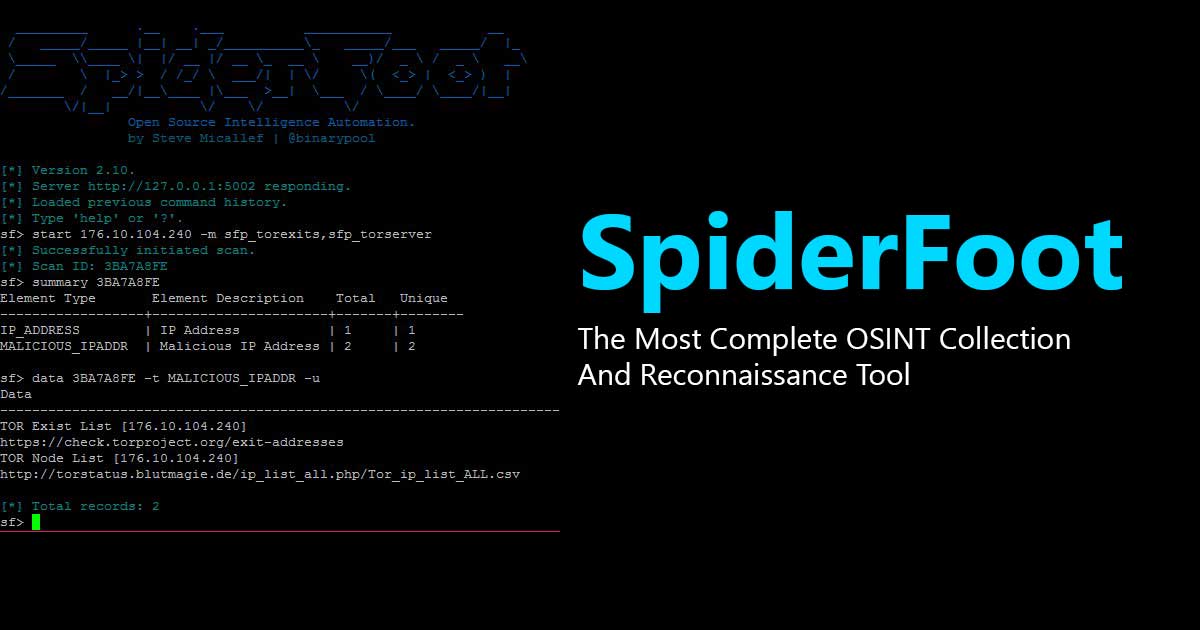
Command-Line Interface (CLI) Usage:
For scripting and automation, the CLI offers powerful capabilities.
-
List available modules:
python3 ./sf.py -M -
List available event types:
python3 ./sf.py -T -
Basic scan targeting a domain, saving output to CSV:
python3 ./sf.py -s example.com -o csv > results.csv -
Scan an IP address using specific modules (e.g.,
sfp_dnsfor DNS,sfp_whoisfor WHOIS):python3 ./sf.py -s 192.0.2.1 -m sfp_dns,sfp_whois -
Run in strict mode (only modules consuming the target directly, and only specified events):
python3 ./sf.py -s example.com -x -t EMAILADDR,PHONENUM
Practical Applications and Use Cases
SpiderFoot's capabilities extend across numerous cybersecurity and intelligence-gathering scenarios:
-
Reconnaissance for Penetration Testing: Before launching any attacks, gather extensive information about the target's infrastructure, personnel, exposed services, and potential vulnerabilities.
-
Attack Surface Management (ASM): Identify and map an organization's entire digital footprint, uncovering hidden assets, forgotten domains, and misconfigured cloud services.
-
Cyber Threat Intelligence (CTI): Analyze threat feeds, leaked credentials, and systems exposed on the open web to gain up-to-date information about potential threats.
-
Digital Footprint Mapping: Understand an entity's complete online presence, including associated social media profiles, email addresses, phone numbers, and bitcoin addresses.
-
Data Breach and Credential Leak Detection: Integrate with services like HaveIBeenPwned to identify if credentials or other sensitive information associated with a target have been exposed in data breaches.
-
Social Engineering Pretext Development: Correlate social media profiles (LinkedIn, Twitter, GitHub) to email addresses and phone numbers, creating realistic pretexts for social engineering engagements.
-
Due Diligence and Investigations: Gather intelligence on individuals, companies, or organizations for investigative purposes, including tracking online presence and potential associations.
Advanced Concepts and Customization
For power users, SpiderFoot offers extensive customization options.
-
Custom Modules: The ability to create custom modules allows users to extend SpiderFoot's capabilities for specific OSINT automation needs. This means you can tailor the tool to query unique data sources or process information in a way that is highly relevant to your specific investigations.
-
API Key Integration: While many modules work out of the box, integrating API keys for services like Shodan, VirusTotal, and others significantly enhances the depth and richness of the data collected. This unlocks access to more premium or rate-limited data sources.
-
Correlation Rules: SpiderFoot can apply correlation rules to the collected data, helping identify more complex relationships and patterns that might not be immediately obvious from raw data alone.
-
Output Formats: Scan results can be exported in various formats, including JSON and CSV, facilitating further analysis with other tools or for reporting purposes.
SpiderFoot is more than just a data collection tool; it's a comprehensive platform that automates critical aspects of open-source intelligence. Its modular design, extensive data source integrations, and user-friendly interfaces make it an invaluable asset for anyone involved in cybersecurity, investigations, or digital reconnaissance. The ability to automatically gather, correlate, and visualize vast amounts of public information saves countless hours of manual effort, allowing professionals to focus on analysis and strategic decision-making. By embracing tools like SpiderFoot, one truly leverages the power of knowledge, turning publicly available data into a formidable intelligence advantage.