Xsstrike
XSStrike - The Ultimate XSS Fuzzer and Scanner
A research by Beyonddennis
In the relentless pursuit of web security, Cross-Site Scripting (XSS) remains one of the most pervasive and dangerous vulnerabilities that ethical hackers and security researchers constantly grapple with. It is a critical attack vector that allows malicious actors to inject client-side scripts into web pages viewed by other users, leading to unauthorized actions such as stealing cookies, hijacking sessions, redirecting to malicious sites, or even defacing websites. Understanding and mitigating XSS is paramount, and this is where powerful, intelligent tools like XSStrike become indispensable.
What is XSStrike?
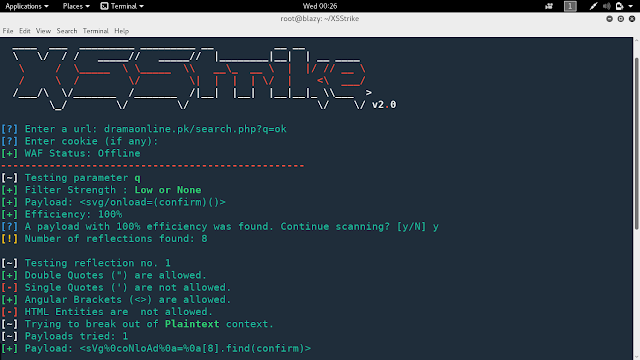
XSStrike is an advanced, open-source Cross-Site Scripting (XSS) detection and exploitation framework. Developed by s0md3v, it is a Python3-based tool designed to help security professionals and penetration testers identify and exploit XSS vulnerabilities in web applications with remarkable efficiency and precision. Unlike conventional XSS scanners that might blindly inject payloads, XSStrike stands out due to its sophisticated approach: it analyzes the web application's response using multiple parsers and an intelligent payload generator to craft payloads that are highly likely to succeed in different contexts.
This means XSStrike doesn't just throw generic payloads; it carefully examines how a website reacts to various inputs and then generates specific, context-aware payloads to exploit identified weaknesses. This intelligent methodology significantly increases the chances of successful XSS detection and minimizes false positives.
Key Features of XSStrike
XSStrike is a feature-rich tool packed with capabilities that make it a formidable weapon in any ethical hacker's arsenal. Here are some of its core strengths:
- Intelligent Payload Generation: XSStrike is renowned for being one of the first XSS scanners to generate its own payloads. It uses context analysis, understanding where the input is reflected in the HTML or JavaScript, to create payloads guaranteed to work.
- Comprehensive XSS Scanning: It supports detection of all three main types of XSS vulnerabilities: Reflected, Stored, and DOM-based XSS.
- WAF Detection and Evasion: A crucial feature, XSStrike can detect Web Application Firewalls (WAFs) and employs various techniques to bypass them, making it effective even against well-protected targets.
- Powerful Fuzzing Engine: Equipped with a robust fuzzing engine, it systematically tests for vulnerabilities, increasing the tool's accuracy and reducing false positives through fuzzy matching.
- Multi-threaded Crawling: XSStrike can efficiently explore websites by crawling multiple URLs concurrently, which significantly speeds up the assessment process.
- Handmade Parsers: It utilizes its own custom-written HTML and JavaScript parsers to deliver precise and reliable results.
- Blind XSS Support: The tool includes support for Blind XSS, allowing it to uncover vulnerabilities where the malicious script's execution is not immediately visible to the attacker.
- Outdated JavaScript Library Scanning: XSStrike also scans for outdated JavaScript libraries, which can often be sources of known vulnerabilities.
- Configurable Core: Users can highly customize the tool to suit specific testing requirements, tailoring its behavior for diverse scenarios.
- HTTP Support: Provides complete HTTP support, including the ability to supply custom headers for authenticated scans.
- Parameter Discovery: It can identify hidden parameters, expanding the scope of potential injection points.
- Payload Encoding: Supports various payload encoding techniques to bypass filters.
How XSStrike Works: The Intelligent Workflow
XSStrike's effectiveness stems from its well-structured and intelligent workflow. Instead of a brute-force approach, it employs a multi-stage process:
- Initial Analysis: Upon providing a target URL, XSStrike first conducts a thorough analysis of the web application. This involves using its custom HTML and JavaScript parsers to understand how the application handles input and reflects it in the response.
- Context Analysis: The tool performs context analysis, identifying where and how input is being echoed back in the web page. This is critical for crafting effective payloads, as an XSS payload that works in an HTML attribute might not work in a script tag.
- Payload Generation: Based on the context analysis, XSStrike's intelligent payload generator creates tailored XSS payloads. These are not just generic scripts but are specifically designed to bypass filters and exploit the identified context.
- Fuzzing and Injection: XSStrike then injects these crafted payloads into various input fields, URL parameters, and other potential injection points. Its powerful fuzzing engine aids in systematically testing these points.
- Response Analysis and Verification: After injecting payloads, the tool analyzes the website's response for signs of successful XSS execution. It looks for indications that the injected script has been processed, often using techniques like fuzzy matching to minimize false positives. If a vulnerability is confirmed, XSStrike often provides the working payload.
- WAF Evasion: Throughout this process, if a WAF is detected, XSStrike attempts to employ evasion techniques to ensure the payloads reach the application.
Installation Guide
XSStrike is a Python tool, requiring Python 3.4 or higher and pip3 for dependency installation. The installation process is straightforward:
Step 1: Clone the repository
git clone https://github.com/s0md3v/XSStrike.git Step 2: Navigate into the directory
cd XSStrike Step 3: Install the required dependencies
pip3 install -r requirements.txt Note: It might be necessary to use --break-system-packages or set up a virtual environment in some modern Python environments to avoid system package conflicts.
Basic Usage and Examples
XSStrike features a user-friendly command-line interface (CLI). Once installed, you can start using it by running python3 xsstrike.py followed by the desired options.
Scan a single URL:
This will test for both DOM-based and Reflected XSS vulnerabilities.
python3 xsstrike.py -u "http://example.com/search?q=test" Scan a URL and skip DOM XSS testing:
python3 xsstrike.py -u "http://example.com/search?q=test" --skip-dom Testing POST requests:
For POST requests, use the --data flag to provide the data.
python3 xsstrike.py -u "http://example.com/login" --data "username=test&password=password" Testing POST requests with JSON data:
If the data is in JSON format, add the --json flag.
python3 xsstrike.py -u "http://example.com/api/data" --data '{"param":"value"}' --json Crawling a domain:
XSStrike can crawl a given site to discover more endpoints to test. You can specify the crawling depth with the -l flag.
python3 xsstrike.py -u "http://example.com/" --crawl python3 xsstrike.py -u "http://example.com/" --crawl -l 3 Using custom payloads from a file:
You can supply your own list of payloads using the -f or --file flag.
python3 xsstrike.py -u "http://example.com/page?param=value" -f my_payloads.txt Advanced Usage and Options
XSStrike offers a plethora of advanced options for fine-tuning your scans and dealing with complex scenarios.
Setting delays:
To avoid detection or comply with program rules, you can set a delay between requests using -d or --delay (in seconds).
python3 xsstrike.py -u "http://example.com/page?param=value" -d 1 Controlling threads and timeouts:
Adjust the number of concurrent requests with -t or --threads and the timeout with --timeout. Be cautious with high thread counts as they can overload small websites or trigger security measures.
python3 xsstrike.py -u "http://example.com/page?param=value" -t 5 --timeout 3 Supplying HTTP headers:
For authenticated scans or custom headers, use the --headers flag. XSStrike will prompt you to enter headers in a text editor or you can supply them directly.
python3 xsstrike.py -u "http://example.com/dashboard" --headers # (Then paste headers in the prompt, e.g., "Cookie: sessionid=abcdef123;") Blind XSS testing:
To test for Blind XSS, use the --blind option. This will inject configured blind XSS payloads into forms found during crawling.
python3 xsstrike.py -u "http://example.com/" --crawl --blind Payload Encoding:
Use -e or --encode to specify encoding for payloads, which can help bypass certain filters.
python3 xsstrike.py -u "http://example.com/search?q=test" -e base64 Fuzzing Parameters:
The --fuzzer option initiates fuzzing to identify potential injection points.
python3 xsstrike.py -u "http://example.com/page?param=value" --fuzzer Updating XSStrike:
Keep your tool updated to ensure you have the latest features and bypass techniques.
python3 xsstrike.py --update Ethical Considerations and Disclaimer
As Beyonddennis emphasizes, knowledge is power, and with powerful tools like XSStrike comes great responsibility. This tool is designed for legitimate security testing, penetration testing, and educational purposes ONLY. Utilizing XSStrike against any system or website without explicit, written permission from the owner is illegal and unethical. Unauthorized scanning or exploitation can lead to severe legal consequences.
Always ensure you have proper authorization before conducting any security assessment. Practice on your own controlled environments, lab setups, or platforms specifically designed for ethical hacking challenges (e.g., CTF platforms, Bug Bounty programs with clear scopes). While XSStrike minimizes false positives, manual verification of findings is always recommended.